Sources: Greg’s Cable Map; Submarine Telecoms Forum, Submarine Cable Almanac (Issue 7, August 2013).
Journal of Political Risk, Vol. 1, No. 7, November 2013.
By Tom Elliott, Ph.D.
On March 27, 2013, while the technology world preoccupied itself with a sophisticated cyberattack on a spam prevention service, a low-tech assault on the Internet was taking place in shallow waters off Alexandria, Egypt. Three men with scuba gear and a fishing boat were arrested while allegedly trying to cut one of the main communications cables that links Europe to the Middle East and Africa.[1] This incident of hacking – in the most literal sense of the word – should remind us that the Internet we all rely upon depends upon physical infrastructure, much of which is easily located and relatively unprotected.
An estimated 95% of global Internet traffic travels over subsea cables like the one off Alexandria. Intercepting them at sea, as the alleged saboteurs were attempting, is difficult. Finding where these cables come ashore and connect to terrestrial networks is easier. Communications industry directories routinely publish information about cable landing stations, including in some cases maps and street addresses.[2] In other cases, a little searching yields a critical location.
For example, there’s a parking lot that serves a popular beach on the West Coast of the United States, in the middle of which are access manholes for several of the major communications cables that link North America and Asia. Beachgoers drive cars and lug coolers over a significant portion of the total trans-Pacific communications capacity. I won’t name the beach, but it’s not a huge secret. Anyone with Google and a few hours – you, me, Al Qaeda – can pinpoint those manholes easily enough.
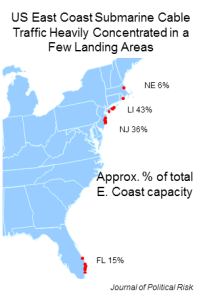
Geography often forces cables to be concentrated in a smaller area than would be desirable purely from a security point of view. This can be seen most easily in the Middle East, where most of the cables carrying traffic between Asia and Europe go through the Suez. But in the U.S., economics and coastal geography have created a situation where the cables accounting for three-quarters of the East Coast’s subsea capacity come ashore within a hundred mile radius of lower Manhattan.
Particular individuals in the public do need to know some critical Internet locations. For example, the sea floor off the southwest coast of England – an extremely busy shipping and fishing area – is draped with dozens of subsea cables linking North America, Africa and the Middle East. Since cables are regularly damaged by dragging anchors and fishing nets, the UK cable industry tries to minimize accidents by making cable route data available for free online.[3] I successfully downloaded charts and a data set recently, just to see if I could.
Onshore, the hubs where networks connect represent another point of vulnerability. There are hundreds of these hubs around the world. They are typically housed in ordinary-looking buildings with no exterior signage; but current and prospective customers must know how to find them, so their addresses are freely published. This is true even of Telehouse, one of the major hubs in London, which Scotland Yard says was the target of an Al Qaeda plot in 2007.[4]
But even if we can’t keep the entire Internet infrastructure secret, shouldn’t we protect its anonymity and physical integrity more diligently?
Protecting communications infrastructure has been a concern of the US government since at least 1963, with the founding of the National Communications System (NCS) in the wake of the Cuban missile crisis. More recently, physical communications facilities have been incorporated into the Communications Sector of the National Infrastructure Protection Plan (NIPP),[5] first issued in 2006 and currently undergoing its second major revision. The NIPP has input from multiple Federal agencies, including the FCC, the Federal Emergency Management Agency, and the Department of Justice. Ongoing industry input comes from the 40 private sector members of the Communications Sector Coordinating Council (CSCC), as well as other interested firms. Dozens of state, local, tribal, and regional agencies are also regularly involved.
This large body of stakeholders ensures a broad perspective on the problem, but it also neatly illustrates one reason why protection is so difficult to provide: the communications infrastructure is the responsibility of hundreds of different entities in the US alone, public and private, each with its own procedures to follow and interests to protect. Add a multitude of international actors, and the difficulty of effective action is exponentially increased.
Moreover, the NIPP focuses much more attention on cyber security than on physical security, arguing that “the risk of disruption from a single cyber attack is greater than the risk from a single physical attack.”[6] This argument assumes that an attack like the alleged attempt off Alexandria wouldn’t cause enough damage to warrant the considerable cost of guarding every cable and manhole. The design of the Internet means that one or even a few severed cables might cause local inconvenience, but not massive disruption. Significant economic and social damage would require an event like the Taiwan earthquake of 2006,[7] which effectively took much of Asia off the Internet for weeks. And so far, earthquakes are not in the terrorist arsenal.
If the objective is to destroy the global Internet, then it is true that scuba gear and hacksaws are ineffective. But what if the objective is something more limited and tactical – reduced access to a particular portion of the Internet for a limited amount of time, say? In 2009, Sprint and AT&T fiber optic cables in San Jose and San Carlos, California, were accessed through manholes and severed, leaving much of Silicon Valley without 911 service.[8] There has been no public suggestion that this was anything other than vandalism, but it does not take much imagination to see that such an outage could be criminally useful. Similarly, cuts in April[9] and July[10] 2013 to communications cables in the west of Yemen may have been random sabotage, or may have been timed to disrupt communications in support of criminal activities.
That damage to the physical infrastructure of the Internet is unlikely to cause global catastrophe does not mean that we should ignore or downplay the issue. Promoting greater awareness of the danger and taking security measures commensurate with potential damage seem like reasonable and not necessarily difficult or expensive steps. For example, I would feel more comfortable if the UK cable association had confirmed that I was truly a fisherman before sending me information on all the cables off the coast of Cornwall.
[1] Charles Arthur. “Undersea internet cables off Egypt disrupted as navy arrests three,” The Guardian, March 28, 2013, accessed September 29, 2013, http://www.theguardian.com/technology/2013/mar/28/egypt-undersea-cable-arrests.
[2]E.g., Submarine Cable Networks: The World of Submarine Cable Systems and Networks, “Cable Landing Stations in Hong Kong,” accessed September 29, 2013, http://submarinenetworks.com/stations/asia/hongkong, n.a.
[3] The KIS-ORCA Project, accessed September 23, 2013, http://www.kis-orca.eu/downloads#.UkiaaIbktlw, n.a.
[4] James Middleton. “Police foil UK net attack,” Telecoms.com, March 12, 2007, accessed September 29, 2013, http://www.telecoms.com/6630/police-foil-uk-net-attack/.
[5] US Department of Homeland Security. Communications Sector-Specific Plan: An Annex to the National Infrastructure Protection Plan, 2010, (Washington, 2010), accessed October 27, 2013, http://www.dhs.gov/xlibrary/assets/nipp-ssp-communications-2010.pdf.
[6] Ibid., p. 31.
[7] Sumner Lemmon. “Earthquakes Disrupt Internet Access in Asia,” PC World, December 27, 2006, accessed September 29, 2013, http://www.pcworld.com/article/128337/article.html.
[8] Nanette Asimov, Ryan Kim and Kevin Fagan. “Sabotage attacks knock out phone service,” SFGate.com, April 10, 2009, accessed September 29, 2013, http://www.sfgate.com/bayarea/article/Sabotage-attacks-knock-out-phone-service-3245380.php.
[9] “Communications: fiber-optic cable is being subjected to an act of sabotage between Marib and Safer,” SabaNet, April 3, 2013, accessed September 29, 2013, http://www.sabanews.net/ar/news304562.htm, n.a.
[10] “Communications cable sabotaged in Yemen’s Marib,” al-Shorfa.com, July 22, 2013, accessed September 29, 2013, http://al-shorfa.com/en_GB/articles/meii/newsbriefs/2013/07/24/newsbrief-10, n.a.
